Salesforce Data Security: Protect & Secure Business Data

Salesforce is a powerful platform that stores and manages critical business data, making security a top priority. Having weak security measures can cause data breaches, unauthorized access, and compliance failures, which may lead to financial and reputational damage. This article explores key threats, security models, best practices, and an actionable checklist to help safeguard your Salesforce environment.
Common Security Threats & How to Prevent Them
Common Administrator Mistakes
Over-Permissioning Users: Granting excessive permissions can expose sensitive data, creating security gaps that malicious actors can exploit. Administrators should carefully review user roles and limit access based on necessity, using the Principle of Least Privilege.
Incorrect Sharing Rules: Improperly configured sharing settings can grant access to unauthorized users.Regularly reviewing sharing rules and settings ensures that only the right users can access records.
Inactive User Accounts: Inactive user accounts that are still accessible pose a security risk because attackers can exploit them for unauthorized access. Admins should regularly review and deactivate or reassign unused accounts.
Major Cyber Threats
Phishing Attacks: Hackers use deceptive emails and fake login pages to trick employees into revealing their Salesforce credentials. These attacks often appear legitimate, being similar to internal communications or well-known services. If credentials are compromised, attackers can access accounts, change data, and commit fraud. To reduce this risk, organizations should train employees to spot phishing, use Multi-Factor Authentication (MFA), and set up advanced email filters to block threats.
OAuth Token Vulnerabilities: Many third-party applications integrate with Salesforce using OAuth tokens, allowing seamless data exchange. However, if these tokens are over-permissioned, they can provide attackers with broad access to Salesforce data. If a token is compromised, it can be used to extract sensitive information without needing login credentials. To prevent this, administrators should grant OAuth tokens only the minimum necessary permissions, regularly review active integrations, and revoke unused tokens.
Excessive API Access: Salesforce APIs enable automated data retrieval and integration with external systems. However, if API access is not properly monitored and restricted, it can lead to unauthorized data extraction. Organizations should restrict API access, set rate limits to prevent data theft, and use Salesforce Shield Event Monitoring to detect unusual activity.
How to Mitigate These Risks
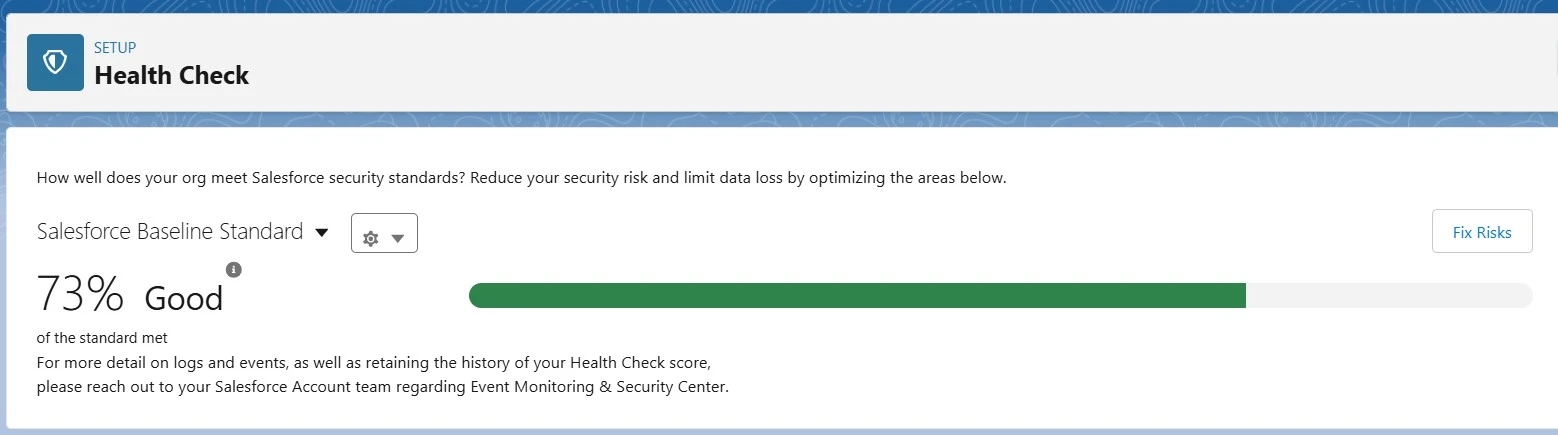
- Use Salesforce Health Check to detect and resolve security incorrect setup.
- Salesforce Health Check provides a centralized security dashboard that highlights risks and provides recommendations to improve security settings.
- Administrators should regularly run Health Check to identify weaknesses in password policies, session settings, and data access controls.
- Implement IP Restrictions & Login Flows to control access.
- IP restrictions ensure that users can only access Salesforce from approved locations, reducing the risk of unauthorized access.
- Login Flows allow administrators to customize access processes, such as requiring additional verification steps for users accessing from unknown networks.
- Monitor and Audit Data Exports with tools like XL-Connector to track and control data movement securely.
- Unauthorized data exports pose a significant risk of data leakage and compliance violations.
- XL-Connector securely exports and imports data by controlling access through the user’s Role/Profile combination.
- All communications between XL-Connector and Salesforce.com are encrypted using a secure HTTPS connection with TLS 1.3, ensuring safe data export and import.
Key Levels of Data Security in Salesforce
Object-Level Security
Object-level security controls access to entire objects (such as Accounts, Opportunities, or Custom Objects) within Salesforce. Access to objects is managed using Profiles and Permission Sets.
Profiles define the base level of access for users, specifying which objects they can view, edit, delete, or create.
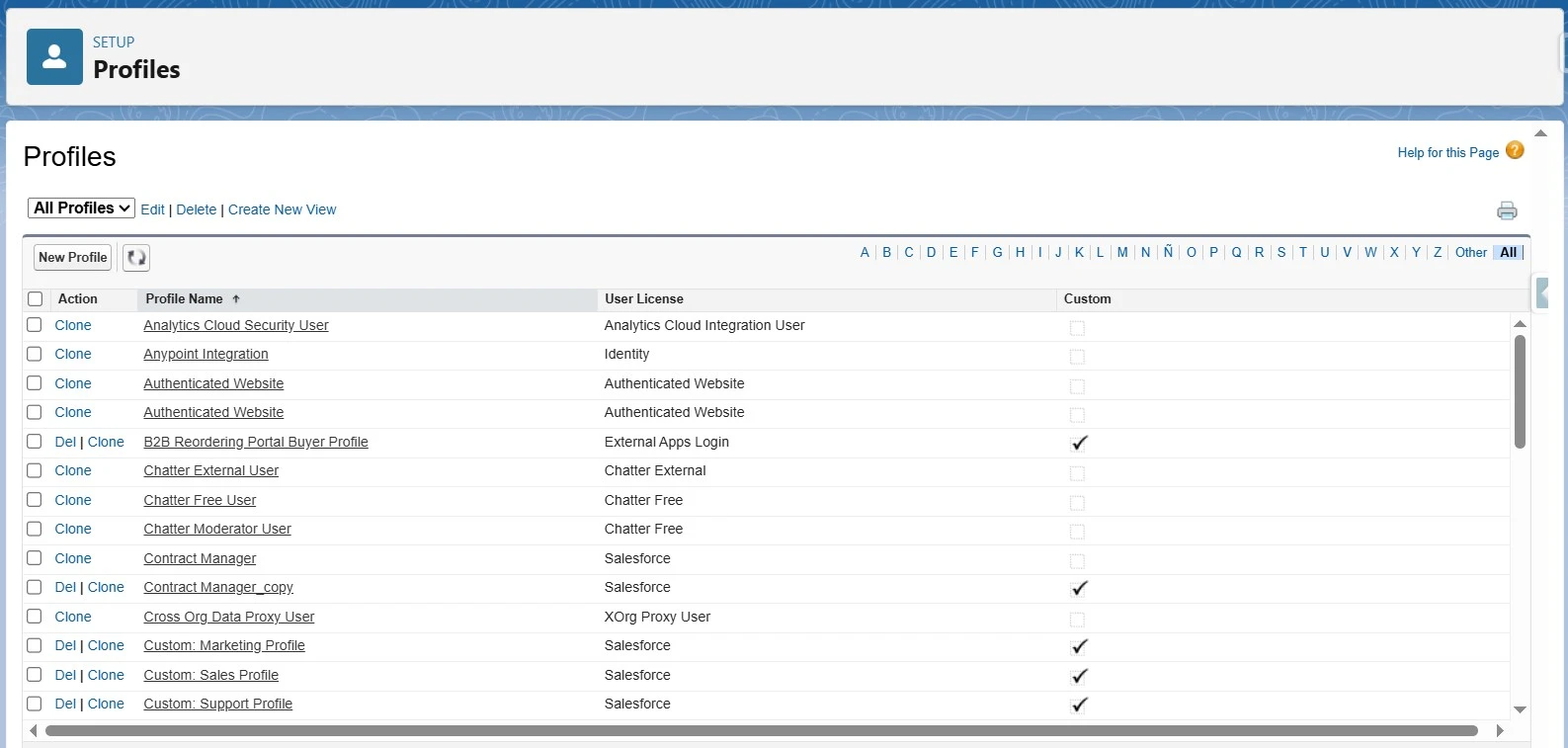
Permission Sets provide additional access to specific objects without modifying a user’s profile, allowing for greater flexibility.
Administrators should follow the Principle of Least Privilege (PoLP) by giving users only the access they need for their role.
XL-Connector can help manage this with its ‘Manage Object-Access Security’ feature.
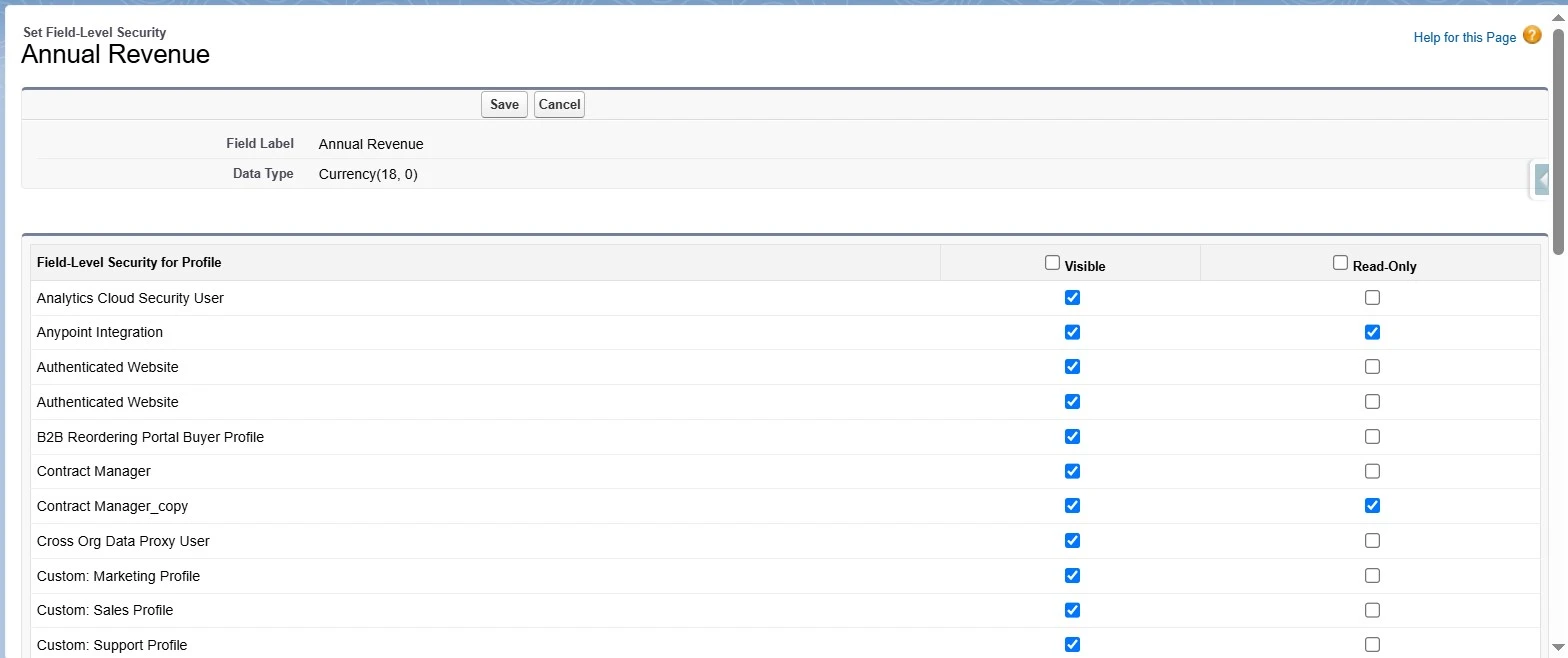
Field-Level Security
Field-level security ensures that users can only access the necessary fields within an object. Even if a user has access to a record, field-level security determines which fields are visible, editable, or hidden:
- Field visibility is configured at the Profile and Permission Set level.
- Organizations handling sensitive information should restrict access to confidential fields.
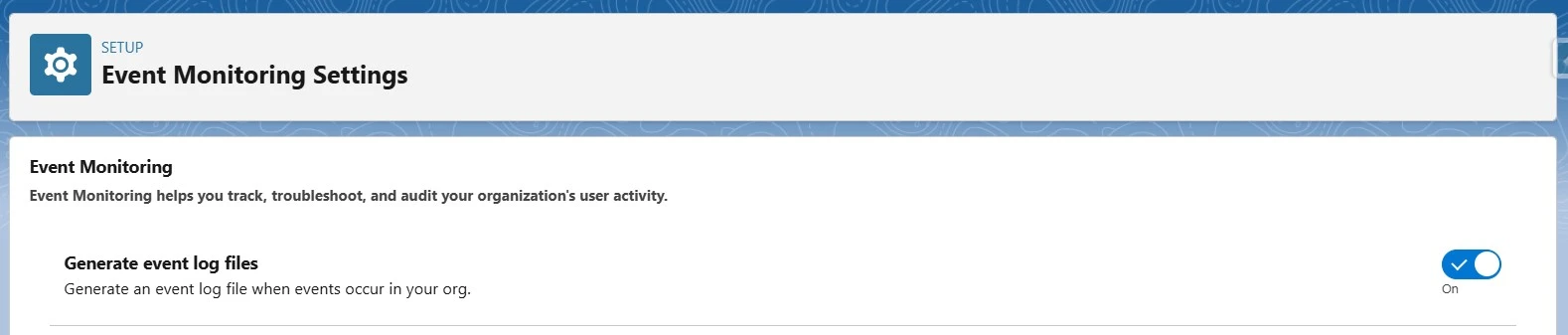
- Enable Event Monitoring to detect suspicious activity.
- Handling field-level security manually across multiple objects can be challenging. XL-Connector’s ‘Manage Field-Level Security’ feature streamlines this task, allowing admins to review and update field permissions for multiple profiles and permission sets at once.

Record-Level Security
Record-level security determines which individual records users can access within an object. Even if a user has access to an object, they may not have access to every record within it. Salesforce provides multiple methods to manage record-level security:
Organization-Wide Defaults (OWD): Defines the basic visibility users will have for records (e.g., Private, Public Read-Only, or Public Read/Write).
Role Hierarchies: Allows users higher in the hierarchy to access records owned by subordinates.
Sharing Rules: Extends record access based on user groups, roles, or criteria.
Manual Sharing: Enables users to grant specific record access on an as-needed basis.
Implementing proper record-level security configurations prevents unauthorized access and protects sensitive business data from exposure.
Best Practices for Salesforce Data Security
Apply the Principle of Least Privilege (PoLP)
- Restrict access based on necessity.
- Use permission sets over profiles to grant only required access.
- Avoid using Modify All / View All permissions unnecessarily.
Enable Multi-Factor Authentication (MFA)
- Mandatory for admin and high-privilege accounts.
- Adds an extra layer of security against compromised credentials.
Monitor User Activity & Security Audits
- Use Salesforce Health Check for vulnerability identification.

- Enable Event Monitoring to detect suspicious activity.

Encrypt Sensitive Data
- Implement Salesforce Shield Platform Encryption to secure high-risk data.
- Ensure compliance with industry-specific data protection regulations.
Control API Access & Data Integrations
- Audit OAuth token permissions to prevent over-permissioning.
- Regularly review third-party API integrations for security compliance.
Regular Backups & Data Export Security
Regular, secure backups in Salesforce are essential to protect against accidental data loss or corruption. However, manually handling exports can be inefficient and produce errors. XL-Connector simplifies this process by automating backups and ensuring secure data transfers, allowing administrators to effortlessly maintain data integrity and security.
Meeting Compliance Requirements
Understanding industry regulations ensures proper security configurations:
GDPR
GDPR is a vital regulation focused on protecting personal data and privacy, imposing severe fines for non-compliance. It emphasizes transparency, accountability, and individuals’ rights over their personal data, such as the right to access, rectify, or erase it.
Salesforce helps organizations meet GDPR compliance by offering features like data encryption, consent management, role-based access control, audit trails, and the ability to respond to data subject requests. These tools ensure secure data handling, facilitate data retention and deletion, and support breach notifications, significantly reducing legal and reputational risks.
HIPAA
HIPAA is a crucial U.S. regulation that protects the privacy and security of personal health information (PHI), with severe penalties for non-compliance. Violations can lead to legal risks, reputational damage, and loss of trust.
Salesforce supports HIPAA compliance by offering features like data encryption, role-based access controls, audit trails, data retention and deletion policies, and Business Associate Agreements (BAAs). These tools help safeguard PHI, ensure secure data handling, monitor access, and facilitate breach notifications, significantly reducing the risks of non-compliance and protecting sensitive patient data.
SOC 2
SOC 2 is a critical framework for managing data securely, ensuring privacy, confidentiality, integrity, and availability of customer data. Non-compliance can damage an organization’s reputation, erode trust, and lead to business disruptions.
Salesforce helps meet SOC 2 compliance by offering features like data encryption, role-based access controls, audit trails, incident response tools, and system monitoring. These capabilities ensure secure handling of sensitive data, track access and changes, and maintain operational effectiveness, helping organizations demonstrate their commitment to data security and mitigate risks of data breaches and reputational harm.
Final Security Checklist & Action Plan
User Access Control
- Audit Profiles, Permission Sets, and Role Hierarchies.
- Disable or reassign inactive accounts.
Data Visibility & Sharing
- Check Organization-Wide Defaults (OWD).
- Validate Sharing Rules & Manual Sharing settings.
Authentication & Login Security
- Enforce MFA for all high-privilege users.
- Set IP restrictions & Login Flows.
Monitoring & Incident Response
- Enable Event Monitoring & Login History Tracking.
- Conduct regular security audits and review access logs.
API & Integration Security
- Restrict OAuth token permissions.
- Audit and monitor all third-party integrations.
Regular Backups & Data Export Security
- Maintain secure, encrypted backups.
- Use XL-Connector for controlled data exports ensuring secure backups, audit-ready compliance tracking, and easy data retrieval for reporting or recovery.
Conclusion
Salesforce data security is an ongoing process requiring continuous monitoring and proactive best practices. By implementing these security strategies, businesses can minimize risks and prevent unauthorized access. XL-Connector adds an extra layer of security, ensuring safe backups and controlled data management.

Xappex CRM data management solutions
Looker Studio for Salesforce
Connect Salesforce reports and queries to your Google Data Studio dashboards.

Excel Merge
Calculate advanced Excel models. Generate Excel documents based on Salesforce data. All with a single click from a Salesforce record page.